Mastering Access: Navigating RBAC in Azure Virtual Desktop
In today’s cloud-first world, access control isn’t just about security.
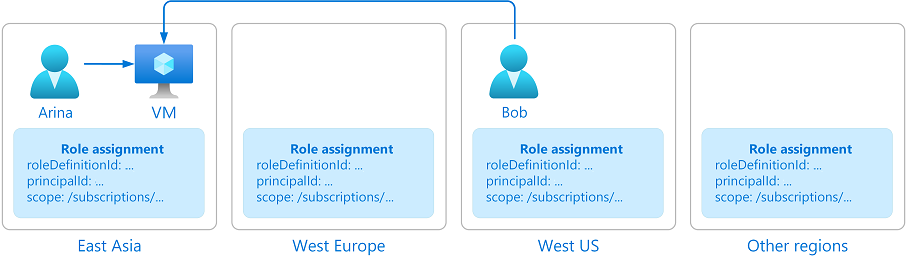
Table of Contents
Introduction
In today’s cloud-first world, access control isn’t just about security - it’s about efficiency. Without the right permissions in place, administrators can struggle, users can get locked out, and security gaps can emerge. That’s where Azure RBAC comes in.
Understanding Role-Based Access Control (RBAC)
RBAC is a permissions model that ensures that users have access to the resources they need based on their roles. RBAC improves the security posture of an organisation and streamlines permissions.
Think of RBAC like a traditional British pub. The bar staff can access the till and drinks, while the chef has access to the kitchen and ingredients. A customer, however, can only order drinks - they can’t walk behind the bar. This structure ensures that everyone has just the right access to do their job efficiently, keeping the pub (or in this case, your Azure environment) running smoothly and securely.
AVD Management: Admin Roles Demystified
Assigning the right admin roles is crucial for managing AVD efficiently. Too much access can introduce security risks, while too little can slow down operations. Below is a breakdown of key roles and what they allow administrators to do.
| Role Name | Description |
|---|---|
| Desktop Virtualization Contributor | Manage all AVD resources except user assignments. |
| Desktop Virtualization Reader | View all AVD resources without making changes. |
| Desktop Virtualization Host Pool Contributor | Manage host pools, including session hosts. |
| Desktop Virtualization Application Group Contributor | Manage application groups but not user assignments. |
| Desktop Virtualization Workspace Contributor | Manage workspaces within AVD. |
| Desktop Virtualization User Session Operator | Send messages, disconnect sessions, and log off users from session hosts. |
| Desktop Virtualization Session Host Operator | View and remove session hosts, and change drain mode. |
Step By Step: Assigning Admin Roles in AVD
RBAC role assignments are a core requirement for Azure administrators. Always follow the least privilege principle - grant only the minimum access needed to perform tasks.
For the demonstration, I will be assigning the Contributor role at the Resource Group level.
- Navigate to the Azure Virtual Desktop blade.
- Select the appropriate scope for the Role Assignment:
- If you're assigning the Desktop Virtualization Contributor Role, it can be assigned at a Resource Group level.
- For a more granular approach, select the individual Host Pool, Application Group, or Workspace.
- Click on Access Control (IAM) in the left-hand menu.
- Click on the Add button and select Add Role Assignment.
- In the Role dropdown, select the required role you want to assign.
- e.g. Desktop Virtualization Contributor.

- In the Assign Access to, select User, Group or Service Principal and choose the required user or group.
Entra ID Joined Session Hosts?
Think setting up Entra ID joined session hosts is straightforward? Not so fast. There are a couple of key RBAC requirements and an RDP property tweak you must get right.
I know this is a blog post about RBAC, but since mastering access is our goal, I'll give you the inside scoop on the RDP property we need to change...later.
Firstly, I'm assuming you're using groups to manage AVD user access. If you're not, then stop right here. Go configure access via groups. I'll wait. Done? Great, let's move on.
RBAC - Virtual Machine User Login
The Virtual Machine User Login role is essential for users who need to log into Entra ID joined session hosts. This role grants the necessary permissions for users to access and interact with the virtual machines.
Critically, without this role, users won't be able to establish a remote desktop connection to the session hosts.
To assign this role, follow the instructions provided above, selecting the Virtual Machine User Login role.
Host Pool - RDP Properties
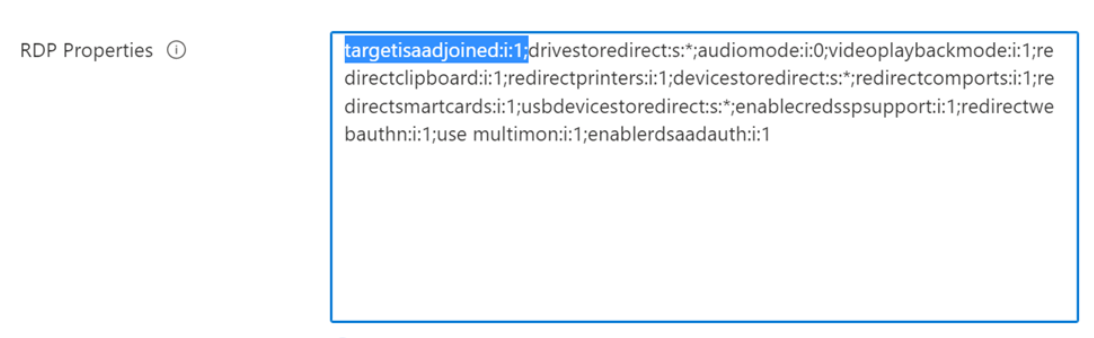
When configuring Entra ID joined session hosts, there's a specific RDP property that needs to be set at the Host Pool level, to ensure proper connectivity. This property is targetisaadjoined:1.
The property allows connections to Entra ID joined session hosts using a username and password. Want to see this in practice? The property should look something like this.
Conclusion
Mastering RBAC in Azure Virtual Desktop is key to securing and streamlining access for both users and administrators. By applying the least privilege principle and configuring the right roles, you ensure a well-managed AVD environment.
Ready to put this into action? Start refining your RBAC strategy today and optimize your AVD setup for efficiency and security!
Need Help? Want to chat? Something I don't know about?






Comments ()